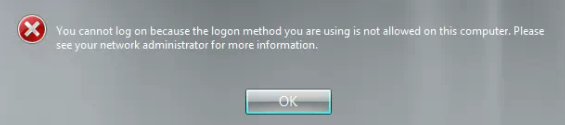
I received the following error message when trying to login to the console of a server this morning:
For future search engine purposes, here’s the text:
You cannot log on because the logon method you are using is not allowed on this computer. Please see your network administrator for more information.
Aside from the usual frustration caused by this message (I am the network administrator), this server is a domain controller and I wondered if I would be able to logon at all.
Fortunately, remote desktop still worked correctly for logon. Looking at the event logs, I saw the following for the failed login:
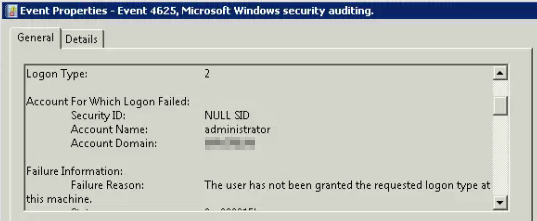 Logon Type 2 is Interactive, or a console logon. The error is indicating that this account somehow didn’t have permission to logon interactively to this computer.
Logon Type 2 is Interactive, or a console logon. The error is indicating that this account somehow didn’t have permission to logon interactively to this computer.
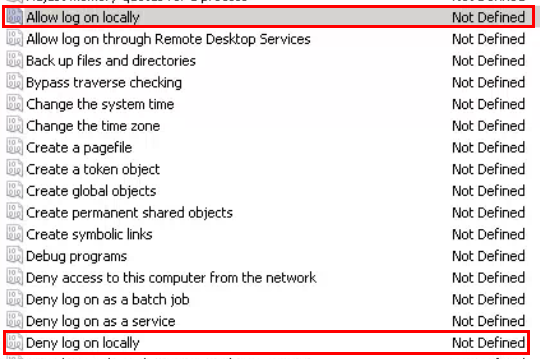
There are a few places to look for this in Group Policy: All of the policies that apply computer settings to this computer. In this environment, the only two policies that applied to the machine were the defaults: Default Domain Policy and Default Domain Controllers Policy.
In both cases, the items to look at are:
Computer Configuration->Policies->Windows Settings->Security Settings->Local Policies->User Rights Assignment->Allow Logon Locally
Computer Configuration->Policies->Windows Settings->Security Settings->Local Policies->User Rights Assignment->Deny Logon Locally
Here’s what those options looked like in Default Domain Policy:
 The options were actually configured in Default Domain Controllers policy:
The options were actually configured in Default Domain Controllers policy:
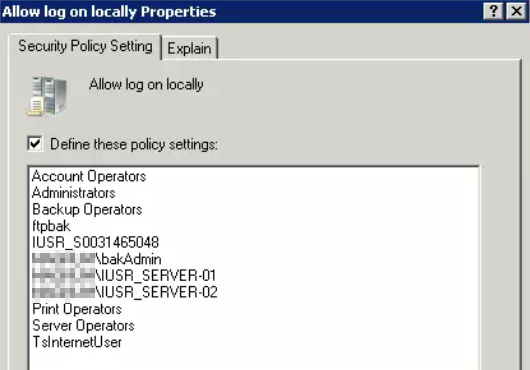
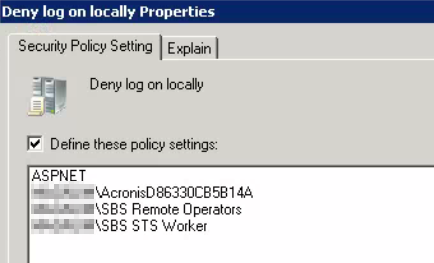 Based on the groups listed in the Allowed section, Administrator should be able to logon locally. I wasn’t sure whether Administrator was in any of those groups, but I checked its group memberships with the following:
Based on the groups listed in the Allowed section, Administrator should be able to logon locally. I wasn’t sure whether Administrator was in any of those groups, but I checked its group memberships with the following:
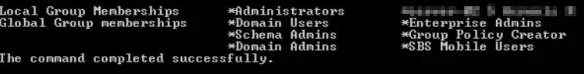 Nothing in there. However, the net use command used in this way won’t show you nested groups. To find those use dsquery piped to dsget (info on this is all over the web. I certainly won’t claim to be the first person to come up with this idea):
Nothing in there. However, the net use command used in this way won’t show you nested groups. To find those use dsquery piped to dsget (info on this is all over the web. I certainly won’t claim to be the first person to come up with this idea):
dsquery user -name “Administrator” | dsget user -memberof -expand
Here are the results:
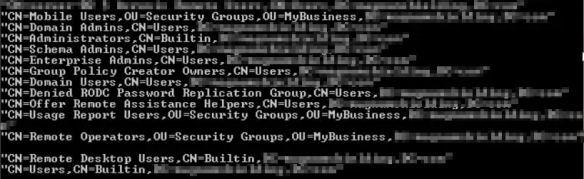 One of the groups stood out here: Remote Operators. It looks suspiciously like SBS Remote Operators from the policy denying local logons.
One of the groups stood out here: Remote Operators. It looks suspiciously like SBS Remote Operators from the policy denying local logons.
In fact, here’s the property sheet for the Remote Operators group:
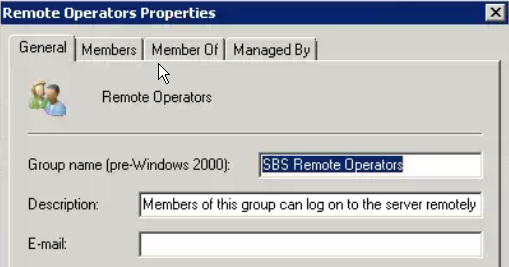 That explained it. Administrator was simply denied permission to logon based on a group membership leftover from SBS. Since this network no longer has SBS, I opted to simply remove that group from the Deny Logon locally option and refresh group policy. After that I was able to logon to the console.
That explained it. Administrator was simply denied permission to logon based on a group membership leftover from SBS. Since this network no longer has SBS, I opted to simply remove that group from the Deny Logon locally option and refresh group policy. After that I was able to logon to the console.